THE STATS ON CYBER SECURITY WITH SMALL & MEDIUM SIZED BUSINESSES.
As a small/medium sized business organization, there are a great many issues in front of your organization when it comes to security. Transformyx is well versed in the frameworks needed to produce a successful business outcome for security, IT support and collaboration to assure that all security plans are in place and functioning. Whether its ALTA, PCI, FINRA, HIPAA, etc., we take security & regulatory compliance very seriously. Our facility in Baton Rouge is only one of two in the entire State of Louisiana that is SSAE 17 and SOC 2 Compliant, and as such, we are trusted by organizations in healthcare, law, education and more who must adhere to stringent federal and state regulatory commands regarding data integrity and protection. The following is a special report outlining some of the current national statistics on cyber security issues within small and medium business organizations.
Security in the World of the Small & Medium-sized Business Enterprise
When it comes to discussions about cyber security there seems to be an enormous misunderstanding about who is at risk. Thanks to the media and new state and federal regulations, most people only hear about the large-scale data breaches with companies like Target, Dillards, Chase and more. Small and medium sized businesses (SMBs) tend to have a ‘won’t happen to me’ attitude because ‘we’re too small to be a target’. The real truth is that in the last 4 years more and more cyber security threats and attacks are being levied against SMBs. When you have a customer’s Personally Identifiable Information (PII), Personal Health Information (PHI) or any of their Personal Financial Information (PFI), then whether today or next month or next year, you will eventually be a target for an attack.
The smart thing for all SMBs when talking about security in general is to adopt a plan of action that is grounded in a framework that best suits your industry, any regulatory compliance your industry is bound by and how you manage your data. Data includes paper AND digital assets, so this is an across the board type of mentality that can even tie into video surveillance and access control systems in some businesses. In short, security is ‘kind of a big deal’ and should be a top priority for the leadership of any SMB.
The following statistics with commentary will provide some basis for what’s really going on out in the world and we will highlight some industry types that we believe are the most vulnerable and the least prepared for security issues and the fines that may accompany them.
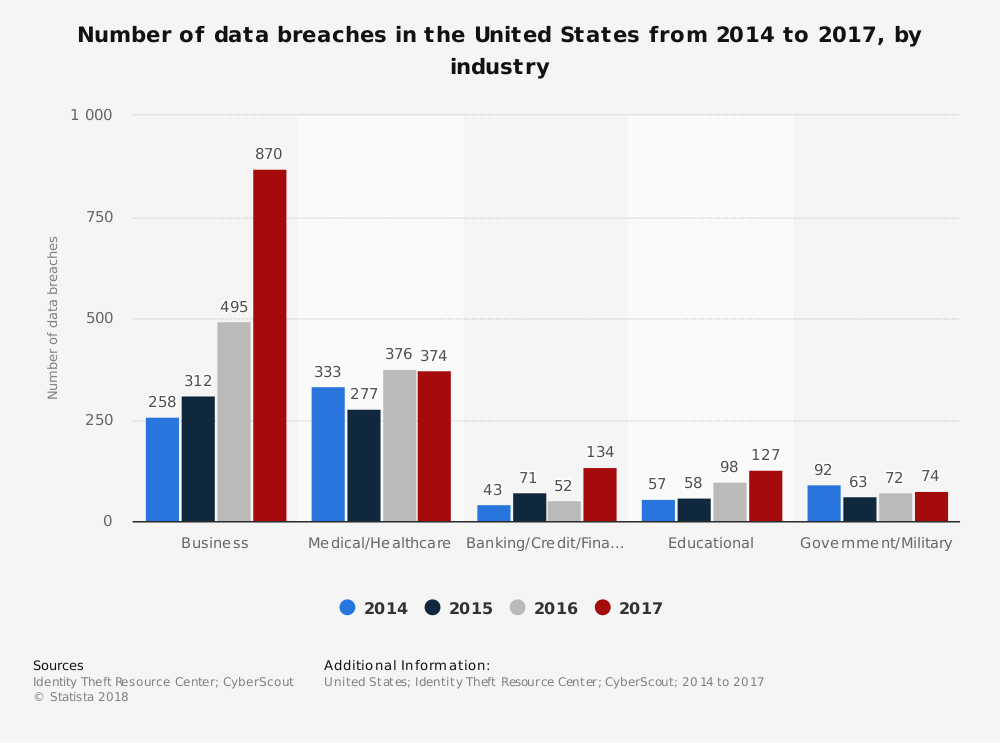
Statistic 1: Number of data breaches in the United States from 2014 to 2017 by industry
The statistic shows the number of data breaches in the United States from 2014 to 2017, by industry. In 2017, the majority of the 1,579 annual data breaches affected business and medical/healthcare organizations, with 870 and 374 data breaches respectively. With the largest increase year over year happening, it becomes clear that smaller organizations are being targeted.
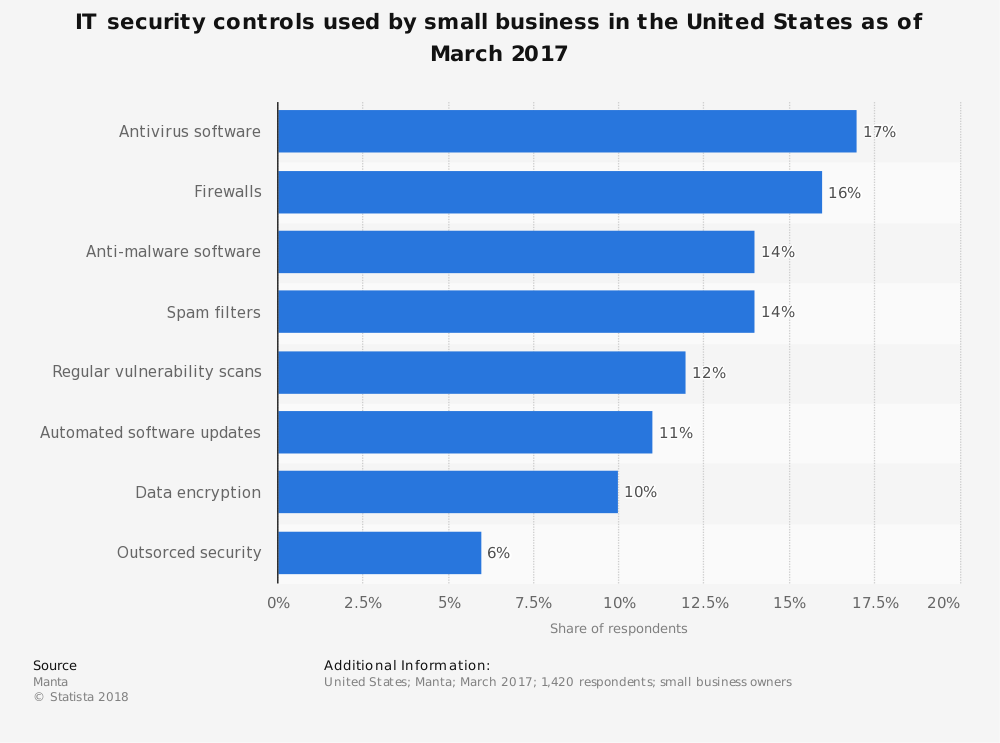
Statistic 2: IT security controls used by small business in the United States as of March 2017
This statistic shows the IT security controls used by small business in the United States as of March 2017. During the survey period, 17 percent of small business owners stated that they used antivirus software. Amazingly, many of these are handling these measures internally and not outsourcing and are forced to manage multiple platforms of technologies which means that whatever staff they have in place must be multi-disciplined. The staffing element is one of the toughest elements of this challenge for SMBs. Outsourcing security means that SMBs can lessen their human asset and technology expenses and trust that the right partner can provide a security framework that decreases expense and exposure.
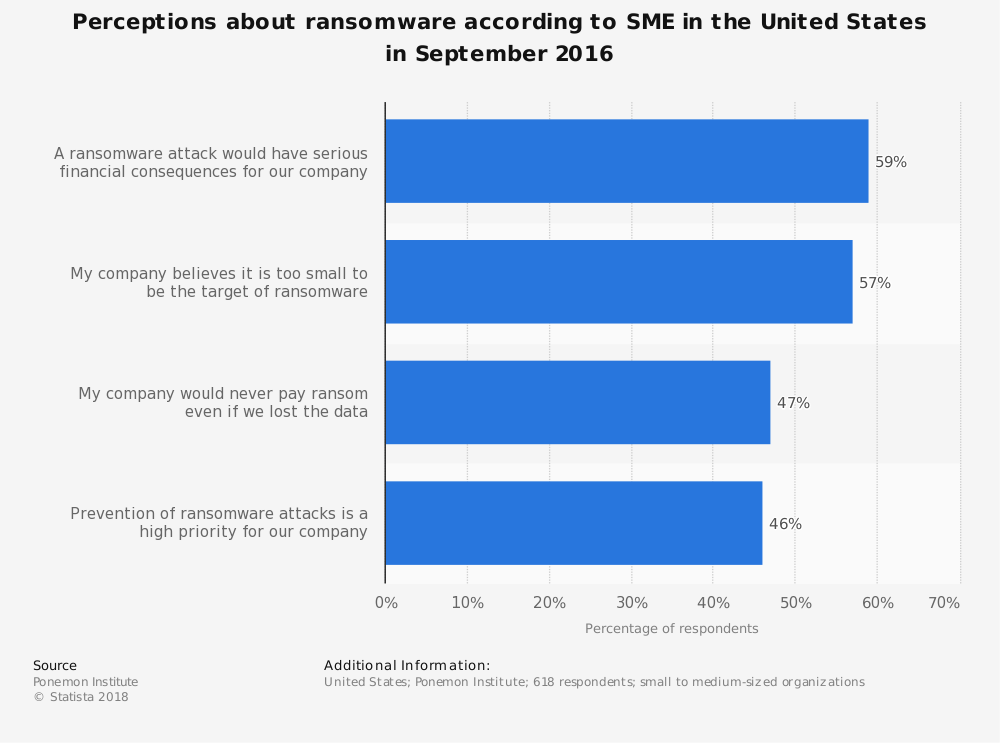
Statistic 3: Perceptions about ransomware according to SME in the United States in September 2016
This statistic depicts the result of a survey where respondents were asked several questions in order to perceive their thoughts towards ransomware in September 2016. According to the survey, 57 percent of respondents believed that their company is too small to be a target of ransomware and only 46 percent of respondents believed that prevention of ransomware attacks is a high priority for their company. The truth here is that it’s not the size of the business but the value of the data being held by the business. A ten person law firm that also does title work can seem small but they may hold hundreds or thousands of client records that contain PCI data, FINRA data, and more. It’s not about the size of your firm. Its about the quantity and types of client data you hold, both in paper and digitally.
What’s the Value of My Data?
According to recent reports from major cyber crime bureaus, the value of personal data is climbing. The chart below shows just a small set of what the value of your data is worth to hackers who want to acquire it and sell it on the black market and dark web.
| Type of Data | Current Value to Hackers |
|---|---|
| Complete Individual Health Record | $1,500 per record |
| Credit Card Records | $50-$75 per record |
| Drivers License Records | $35-$50 per record |
| Social Security Records | $50 per record |
| Legal Records | $500 to $1,000 per record |
And this is just a small sampling of the value of data. Imagine being one of these and thinking about the hundreds to potentially thousands of records and types of information you have on your customers and the damage that could occur from a breach:
- a small organization in healthcare (think non-hospital affiliated like urgent care, independent pharmacy, dentist, etc.) or,
- a law firm (think family law, title, wills & estates, personal injury, etc.), or,
- a small retail store with one or more locations or,
- a restaurant with one or more locations
Breaches and loss can come from employee error, problems with your guest wifi access, a direct attack by a hacker, someone accessing stored paper records or the worst, being fined in a regulatory audit for not being prepared or having inadequate safeguards or framework in place. It becomes easy to see that the need for a proactive security plan for your data should be as important as any IT support you pay for.
In Closing
Cybersecurity is a significant challenge for all businesses. There is no 'silver bullet' to accomplishing it, nor will even the most comprehensive set of safeguards be 100% secure. On the other hand, ignoring the problem or succumbing to myths that cloud thinking on how to tackle the challenge should be avoided.